How to Use a Proxy Server for Enhanced Security and Performance
March 15, 2016What is a Proxy Server Address?
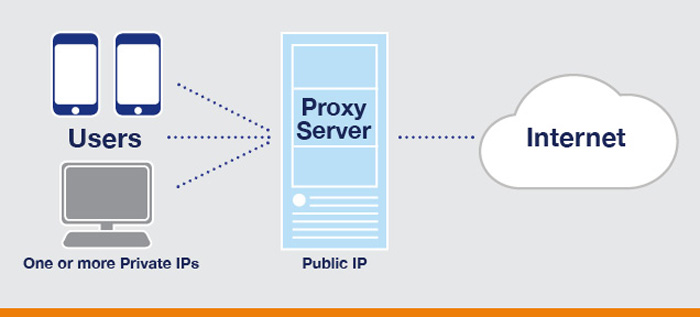
A proxy is a substitute, an alternate, or stand-in. In the Internet world, a proxy server acts as an intermediary between a web browser (computer) with a private IP address and another server on the Internet. A proxy server has its own address, an IP address.
You might run a proxy server for 3 reasons: proxy server for security, proxy server for identity protection or proxy server for load balancing.
Proxy Servers can:
- Obscure a client’s private IP
- Block malicious traffic
- Block specific sites
- Log a server’s activity
- Speed up performance
How to Use a Proxy Server
A proxy server receives requests for information from a particular URL, and passes the request to another server. Then it forwards the answer back to the computer that posed the question.
Think about this analogy.
A receptionist at a dentist’s office gets a call from a patient asking if they can continue taking Tylenol. He asks the dentist, who answers the question. Then the receptionist relays the answer to the patient caller. The receptionist is the proxy.
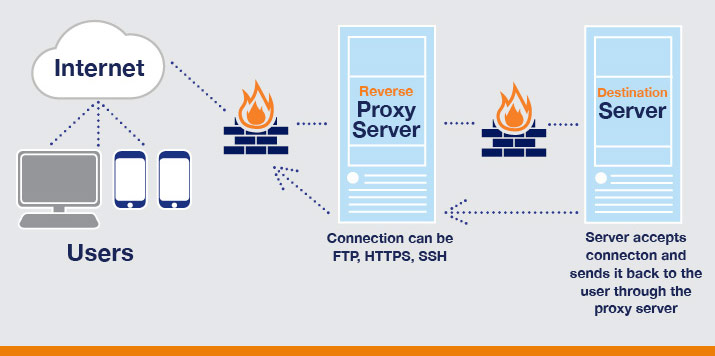
A Reverse Proxy Server Acts as a Buffer
Within an organization, like a college or business, proxy servers can face the Internet (outward) and relay requests from computers on the campus network to destination computers outside the network.
Or, they can face inward, receiving requests for information and sending them to computers located on the campus or businesses network.
Hackers can get to your proxy server – but not the server that is actually running the web software.
How Secure Proxy Servers Boost Security
The Internet can be a nasty place, and you may not want bad people accessing your servers. One way to prevent such access, while at the same time making the information from your servers available, is to run a proxy server.
One primary job of a secure proxy server is to hide your IP address. The proxy server has its own IP, which acts as a shield by masking the user’s IP.
Considering today’s security landscape, the proxy server security can be a valuable extra layer of protection for your sensitive core business systems from prowling Internet forces.
How Proxy Servers Hide Searcher Identity
If you work at the NY Times or MIT, you may not want people to know the databases you’re searching or the people you are talking with on Skype.
So running requests through a proxy server shields end user identity by shielding the identity (IP address) of your computer.
Load Balancing When Demand is High
If a bazillion people are asking to watch the latest episode of House of Cards, it can’t be loaded on just one server. In fact, it’s loaded on dozens of servers all over the world.
But people can access this network of servers using a single URL: www.netflix.com. Netflix runs a proxy server, which balances the requests to each one of those servers so there is no single server overload. It also means that if one of those servers goes down or is taken off-line, Netflix customers can still get to the other servers to see House of Cards. That’s load balancing.
Peering is typically part of the equation to enhance performance and speed.
Privacy
In closing, understanding how to use a proxy server and knowing what makes the proxy server unique is not only its hardware, but its role in the health of your enterprise.
Security—a proxy server is a great way to add a layer between your enterprise and the Internet.
Identity—if you are someone like a journalist or researcher who needs to surf the web anonymously, you can also use a proxy service—such as TOR.
Load Balancing—a proxy server alone is not nearly as effective as one where Peering is usually part of the configuration.